Iso 7498 2 Security Architecture Frameworks
View My Free Estimate Now *By clicking 'View My Free Estimates Now' I authorize security companies, including ADT, Alarm Advisors, Alliance, FrontPoint, LifeShield, MONI, Protect America, Protect Your Home – ADT Authorized Premier Provider, Protection1, SafeStreetsUSA – ADT Authorized Dealer, Guardian Protection Services, Vivint, their dealers and partner companies to contact me about security offers by phone calls and text messages to the number I provided. I authorize that these marketing communications may be delivered to me using an automatic telephone dialing system or by prerecorded message.
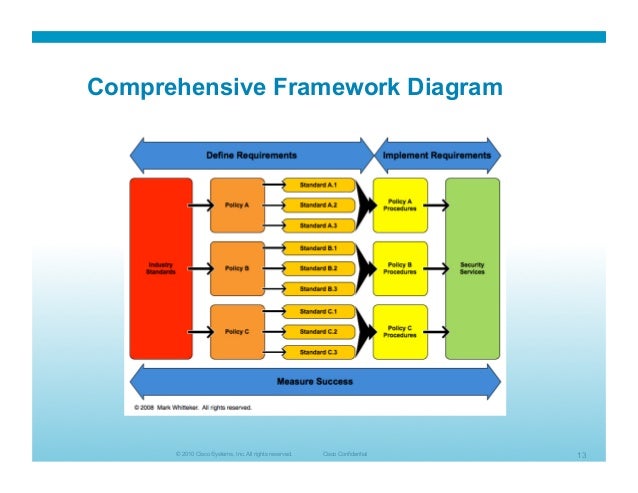

ISO 7498-2 First edition. Part 2: Security Architecture. That part of ISO 7498 establishes a framework for coordinating the development. ISO 7498-2:1989 Preview Information processing systems -- Open Systems Interconnection -- Basic Reference Model -- Part 2: Security Architecture.
I understand that my consent is not a condition of purchase. Privacy Policy This privacy policy was created to let you know what information we collect from you, what we do with it, and to assure you that your information will be respected on our Web site Homesecurityquotes. Windows Xp 64-bit 360 Tage Trial Version Zum Download. Com (referred to herein as 'Provider', the 'Site', 'we' or 'us').
The Provider attempts to protect your privacy to the maximum extent possible. We currently offer users the option of participating in online marketing campaigns to request quotes on products including but not limited to insurance and home security products (referred to herein as 'Services'). By using the Site and the Services, you consent to the following terms. YOUR VISITATION, USE, AND REGISTRATION ON THIS SITE MEANS THAT YOU ACCEPT THE PRACTICES SET FORTH IN THIS POLICY. WE RESERVE THE RIGHT TO MAKE CHANGES TO THE POLICY AT ANY TIME.
YOUR CONTINUED USE INDICATES YOUR AGREEMENT TO THE CHANGES. IT IS YOUR SOLE RESPONSIBILITY TO CHECK BACK REGULARLY FOR UPDATES TO THIS POLICY. This policy covers the following topics: • What personally identifiable information is collected from you through the Site or the Services; • How the information is used; • With whom the information may be shared; • What choices are available to you regarding collection, use, and distribution of the information; and • How you can OPT OUT of receiving marketing information from or providing personal information to Provider. • How you correct errors or inaccuracies in your information. • What information do we collect? Computer Forensics Investigation Procedures And Response Pdf Free. We collect several different types of information from you: • Information collected at registration We collect personal information when you register with us and when you use our Services. We may combine this information about you with information we obtain from our business partners or other companies.
During registration for some of our services, we may require users to give us basic contact information (such as your first and last name, e-mail addresses, and mobile phone number). The information requested on the registration form may change from time to time. Although additional demographic information may be requested at the time of registration, only information marked 'required' is necessary for registration and utilization of our services. We do not accept registrations from persons under the age of eighteen.